If you didn't know, Facebook has a program called White Hat where they invite hackers (and the like) to find security flaws within the social network. If the said hacker reports it, they could be up for a cash reward.
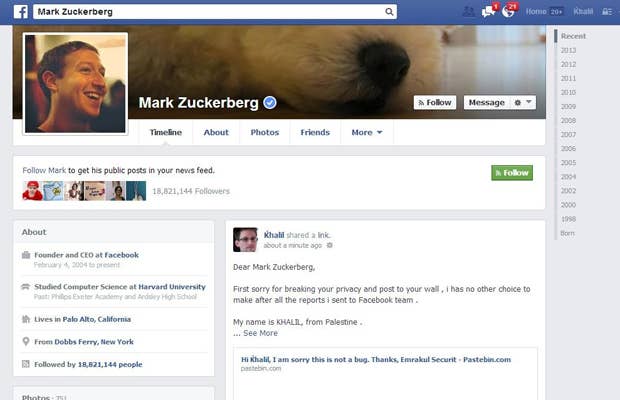
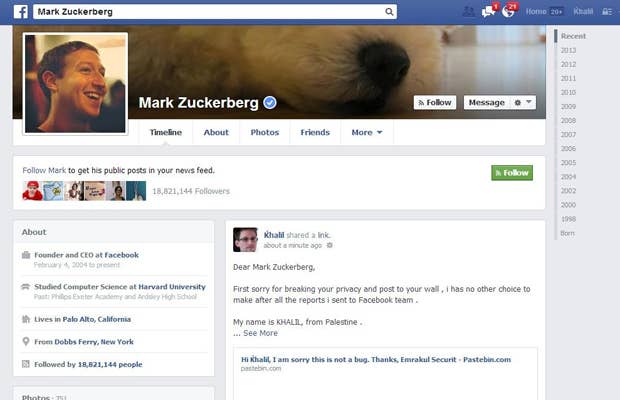
But what happens when you spend time finding a security flaw that Facebook doesn't deem as a flaw? You exploit it, of course, and use it to post on Mark Zuckerberg's Timeline to show him you mean business. This is what Khalil Shreateh, a Palestinian hacker, did when he found out a way to get through Facebook's privacy settings and post on anyone's Timeline, even if you're not friends with the person. So, as in terms with White Hat, he sent in an email about the vulnerability. But one of Facebook's workers couldn't recognize what he was describing.
Shreateh ended up testing his bug by posting to the Timeline of one of Zuckerberg's college friends, but since the Facebook worker who was assigned to check out the report wasn't friends with Zuckerberg's classmate, he couldn't verify it.
In a follow up email, Shreateh tried explaining that, if he wanted to, he could post to Zuckerberg's wall, but he wouldn't because he "respect people privacy [sic]."
After a good amount of time, the Facebook worker finally responded with "I am sorry, this is not a bug."
Shreateh then warned, "ok, that mean [sic] I have no choice other than report this to Mark himself on Facebook."
So, he did (which you can see in the picture above).
Soon afterward, Shreateh's account was suspended for violating Facebook's terms of usage (because, um, you're not supposed to do stuff like that).
"Exploiting bugs to impact real users is not acceptable behavior for a white hat," Matt Jones, a Facebook employee said. "We allow researchers to create test accounts here to help facilitate responsible research and testing. In this case, the researcher used the bug he discovered to post on the timelines of multiple users without their consent."
Sadly, Shreateh won't be getting paid.
Here's a video about how he exploited the security bug:
[via New York Post]